Read Mail Messages via MS Graph APIs
Contents
Read Mail Messages via MS Graph APIs#
A threat actor with the right permissions and credentials can access and collect confidential information of interest right away. One example would be the collection of e-mails. An adversary can use Azure AD registered applications with Mail.Read or Mail.ReadWrite permissions to collect e-mails from a signed-in user mailbox or all mailboxes. This would depend on the type of permission (Delegated or Role) granted to the application.
In this document, we are going to access the mailbox of a user via an application with Mail.ReadWrite delegated permissions.
Table of Contents#
Preconditions#
Authorization:
Resource: Azure Microsoft Graph
Permission Type: Delegated
Permissions
Mail.ReadWrite
Input:
Microsoft Graph OAuth access token
Simulation Steps#
Verify Microsoft Graph Access Token#
We need to make sure our access token has permissions to read mail. You can get that information while getting the OAuth access token with a SAML assertion in the previous step
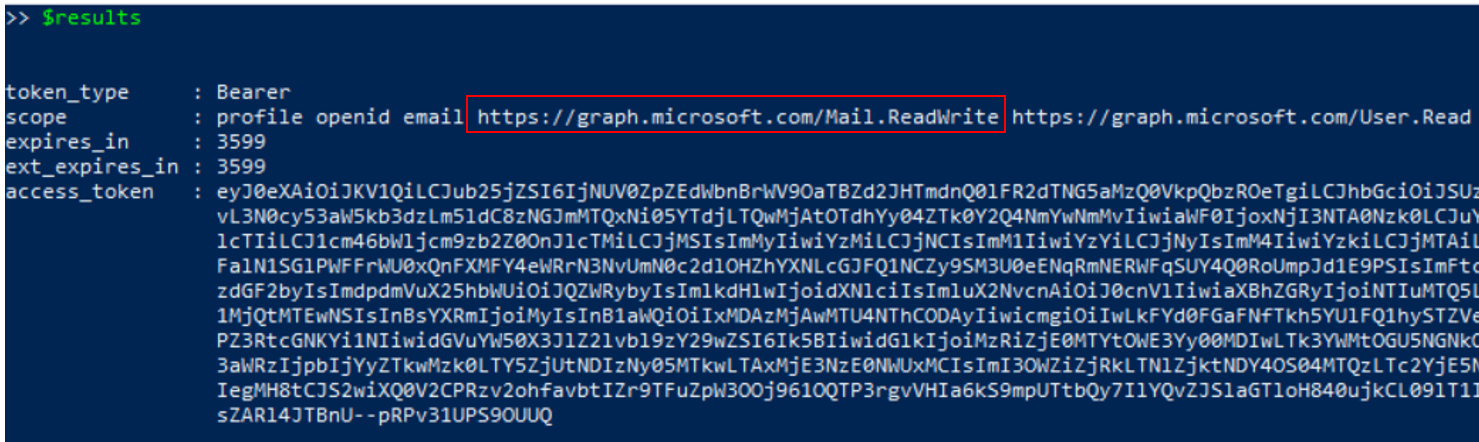
Read Signed-In User Mail#
$uri = "https://graph.microsoft.com/v1.0/me/messages"
$header = @{Authorization = "Bearer $OAuthAccessToken"}
$mailbox = Invoke-RestMethod –Uri $uri –Headers $Header –Method GET –ContentType "application/json"
$mailbox
$mailbox.value[0].from
$mailbox.value[0].subject
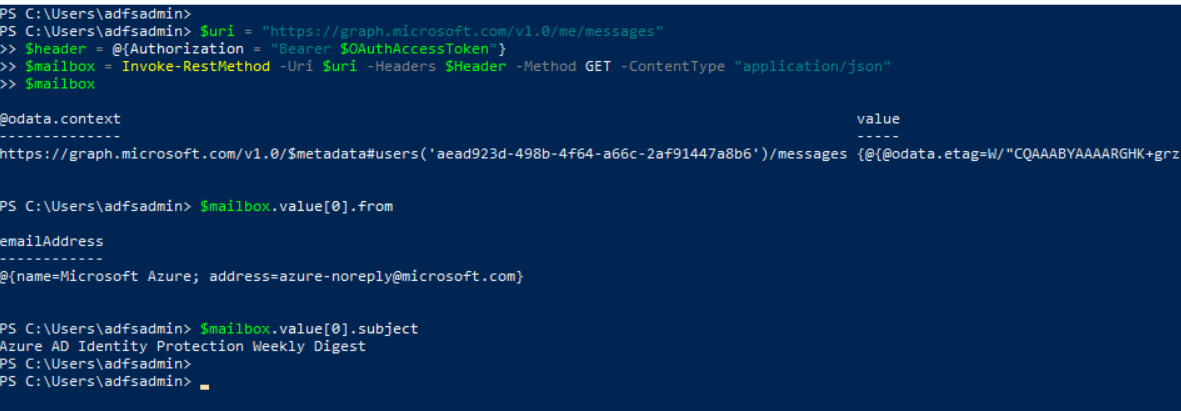
We do not have to parse the messages in this step. The simple action to access the mailbox generates telemetry that we can aggregate and create detections with.
Detection#
Output#
Mail Messages
